CS6250 FINAL EXAM ACTUAL 2025/2026 (QUIZZES - INTERNET SECURITY AND SURVEILLANCE) Q&A
Course:
NETWORK SECURITY
Institution:
NETWORK SECURITY
CS6250 FINAL EXAM ACTUAL 2025/2026 (QUIZZES - INTERNET SECURITY AND SURVEILLANCE) QUESTIONS AND 100% CORRECT ANSWERS A censorship technique can use any combination of criteria based on content, source IP and destination IP to block access to objectio...
After purchase, you get:
✅ Instant PDF Download
✅ Verified answer explanations
✅ Refund if not Satisfied
✅ Prepared for 2025/2026 test cycle
Overview
Learners gain valuable practice with question types commonly used on official CS6250 FINAL ACTUAL / (QUIZZES - INTERNET SECURITY AND SURVEILLANCE) Q&A exams. From multiple-choice to case studies, you'll encounter the full range of formats used in actual assessments. This thorough exposure prevents surprises on test day and builds adaptability in your approach. Students often mention how this variety keeps their study sessions interesting and engaging over weeks of preparation.
Who Is This For?
CS6250 FINAL ACTUAL / (QUIZZES - INTERNET SECURITY AND SURVEILLANCE) Q&A aspirants aiming to build both conceptual knowledge and exam strategy will find this document extremely useful. Many successful candidates have used similar materials in their preparation. The thorough coverage ensures no important topics are missed. Suited to both first-time test takers and repeat candidates, this document helps learners excel at key Exam (elaborations) concepts. People often use it during their final review week. The straightforward approach makes complex topics more accessible.
Related Keywords
Detailed Study Description
Frequently Asked Questions
Document Information
| Uploaded on: | October 31, 2025 |
| Last updated: | November 17, 2025 |
| Number of pages: | 11 |
| Written in: | 2025/2026 |
| Type: | Exam (elaborations) |
| Contains: | Questions & Answers |
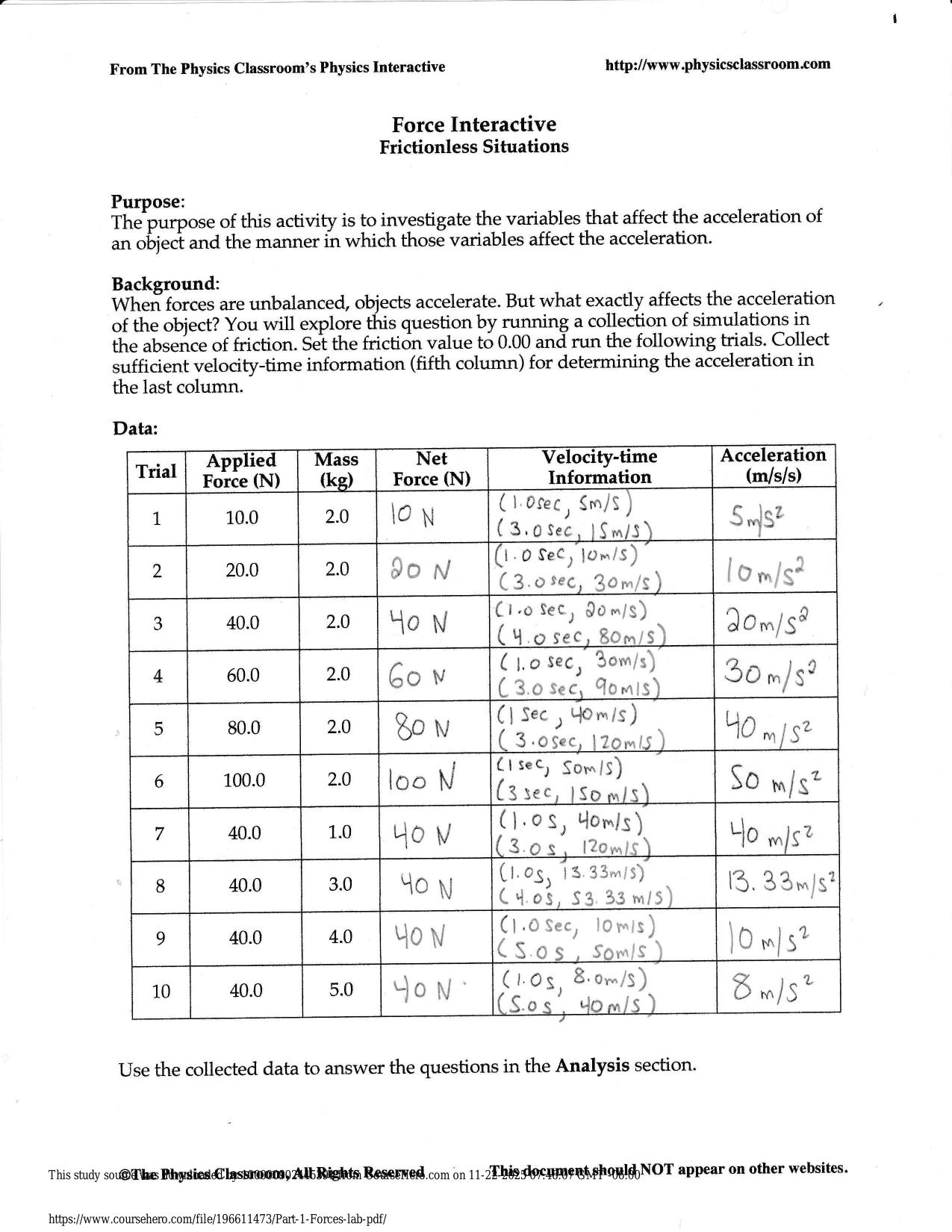
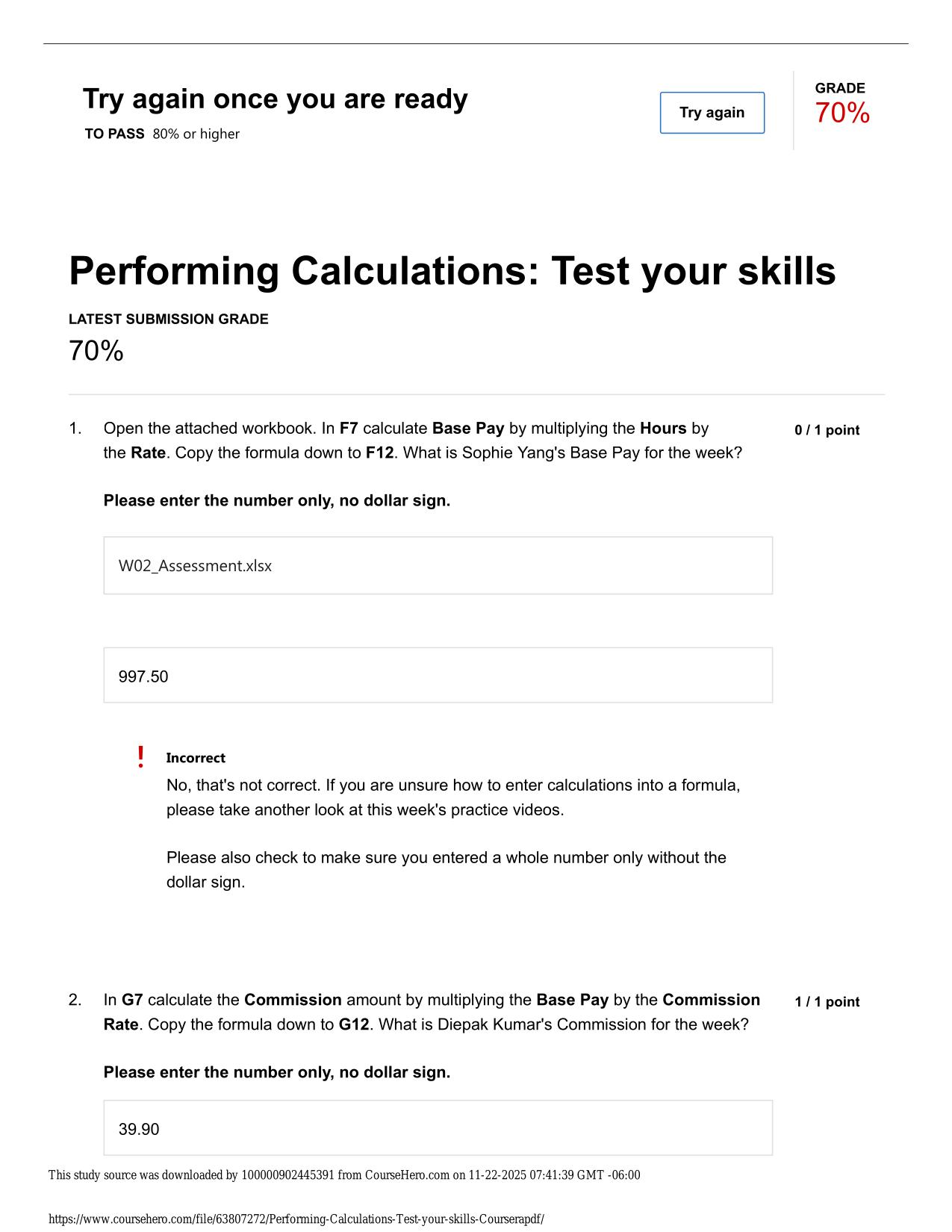
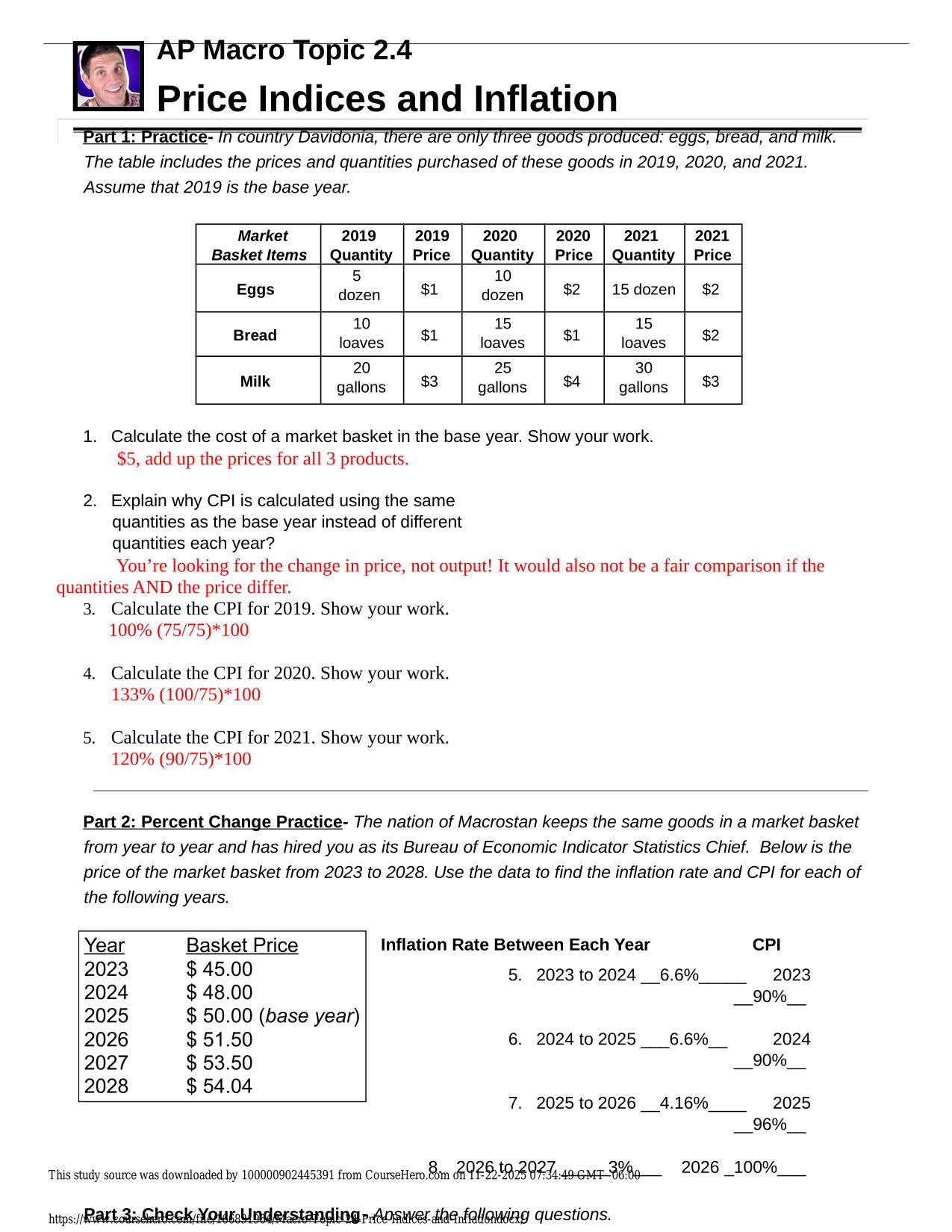
| Tags: | CS6250 FINAL EXAM ACTUAL 2025/2026 (QUIZZES - INTERNET SECURITY AND SURVEILLANCE) QUESTIONS AND 100% CORRECT ANSWERS A censorship technique can use any combination of criteria based on content, source IP and destination IP to block access to objectionable content. (T/F) - Answer -True DNS injection uses DNS replies to censor network traffic based on the source and destination IP address. (T/F) - Answer -False |
Seller Information

AdelineJean
User Reviews (0)
Exam (Elaborations)
$8.00
Bundle Deal! Get all 5 docs for just $17.50
Add to Cart
100% satisfaction guarantee
Refund Upon dissatisfaction
Immediately available after purchase
Available in Both online and PDF
$8.00
| 0 sold
Discover More resources
Available in a Bundle
Inside The Document
CS6250 FINAL EXAM ACTUAL 2025/2026 (QUIZZES - INTERNET SECURITY AND SURVEILLANCE) QUESTIONS AND 100% CORRECT ANSWERS A censorship technique can use any combination of criteria based on content, source IP and destination IP to block access to objectionable content. (T/F) - Answer -True DNS injection uses DNS replies to censor network traffic based on the source and destination IP address. (T/F) - Answer -False With a censorship technique based on packet dropping, all network traffic going to a set of specific IP addresses is discarded. (T/F) - Answer -True When using DNS Poisoning, all traffic passes through a proxy where it is examined for content, and the proxy rejects requests that serve objectionable content. (T/F) - Answer -False When using the Blocking with Resets technique, if a client sends a request containing flaggable keywords, only the connection containing requests with objectionable content is blocked. (T/F) - Answer -True With the Immediate Reset of Connections technique, whenever a request is sent containing flaggable keywords, any subsequent request will receive resets from the firewall for a certain amount of time. (T/F) - Answer -True One of the obstacles to fully understand DNS censorship is the Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com
CourseHero & Studypool Unlocks
Get Unlocked CourseHero and Studypool documents files instantly to your email, simply by pasting your link and clicking "Unlock Now". Learn more on how to unlock here.