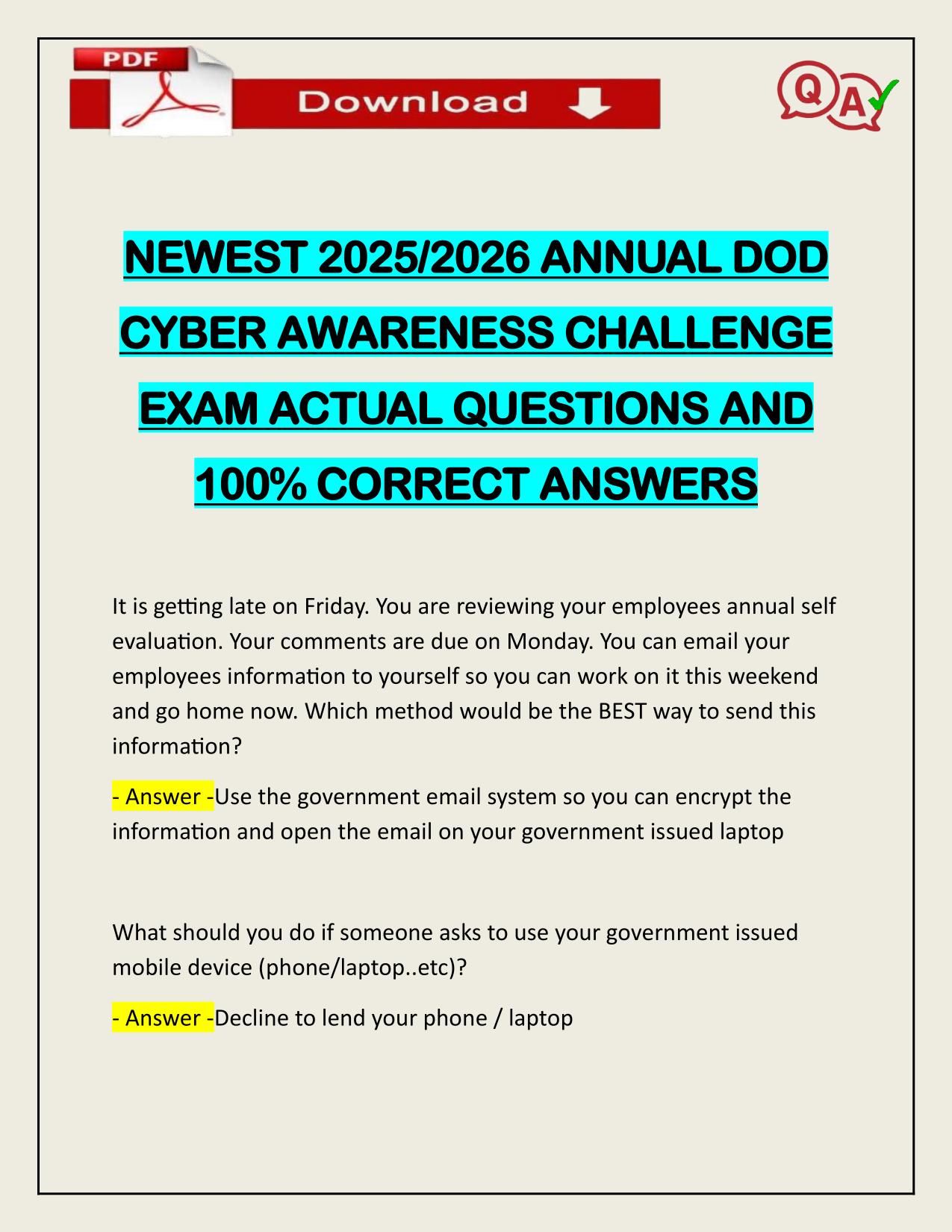
CYBER AWARENESS CHALLENGE ACTUAL 2025/2026 (KNOWLEDGE PRE-CHECK) Q&A
Course:
CYBER AWARENESS CHALLENGE
Institution:
CYBER AWARENESS CHALLENGE
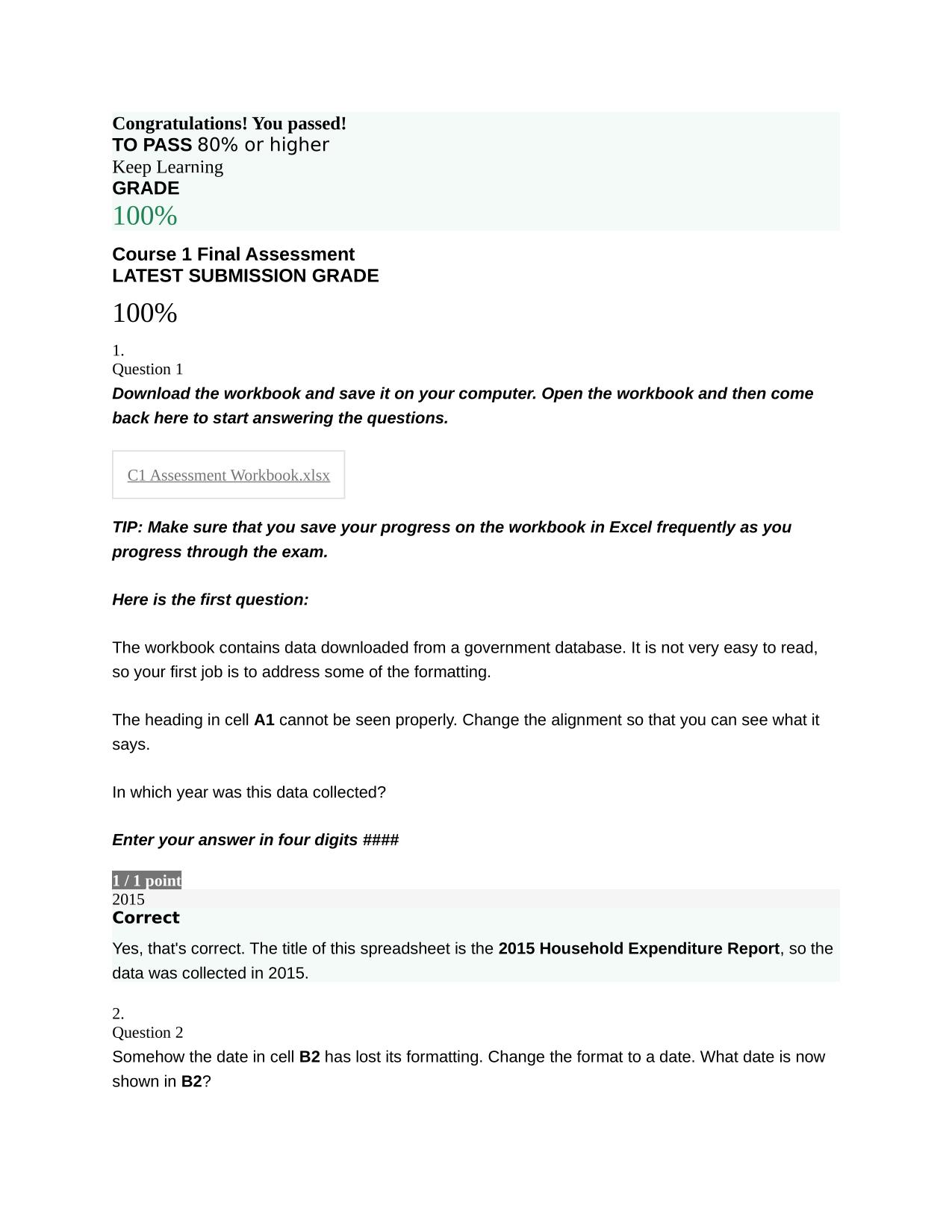
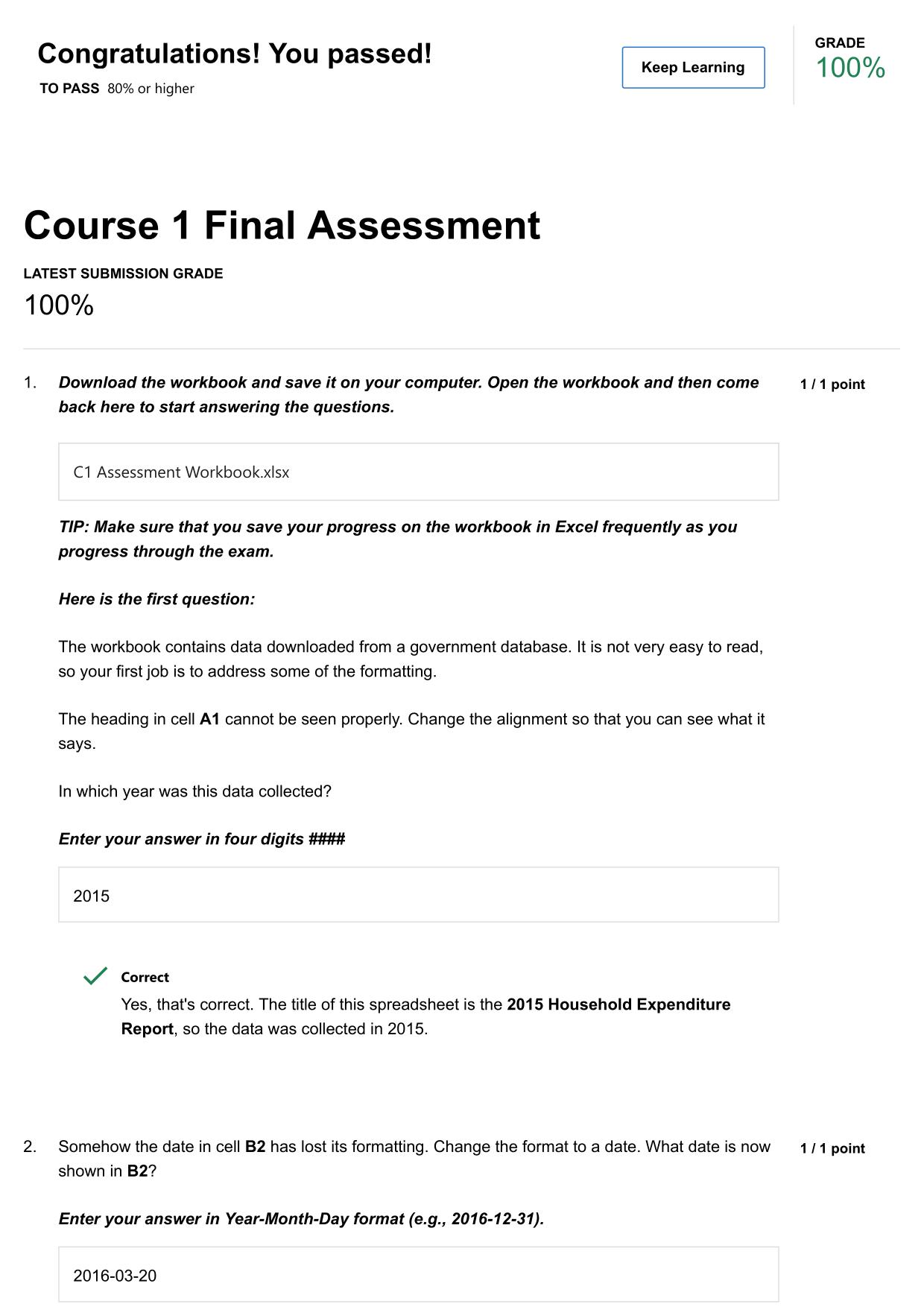
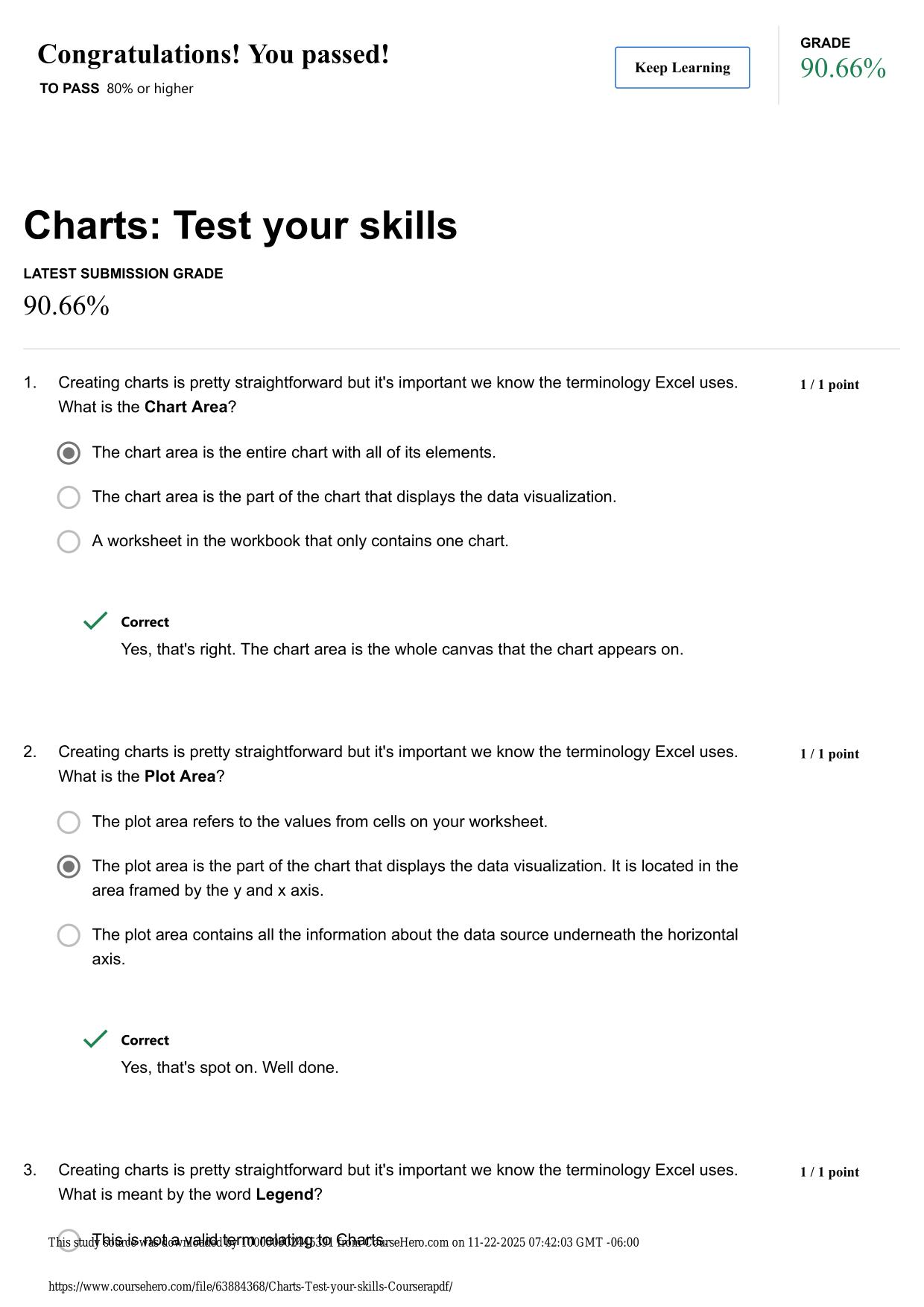
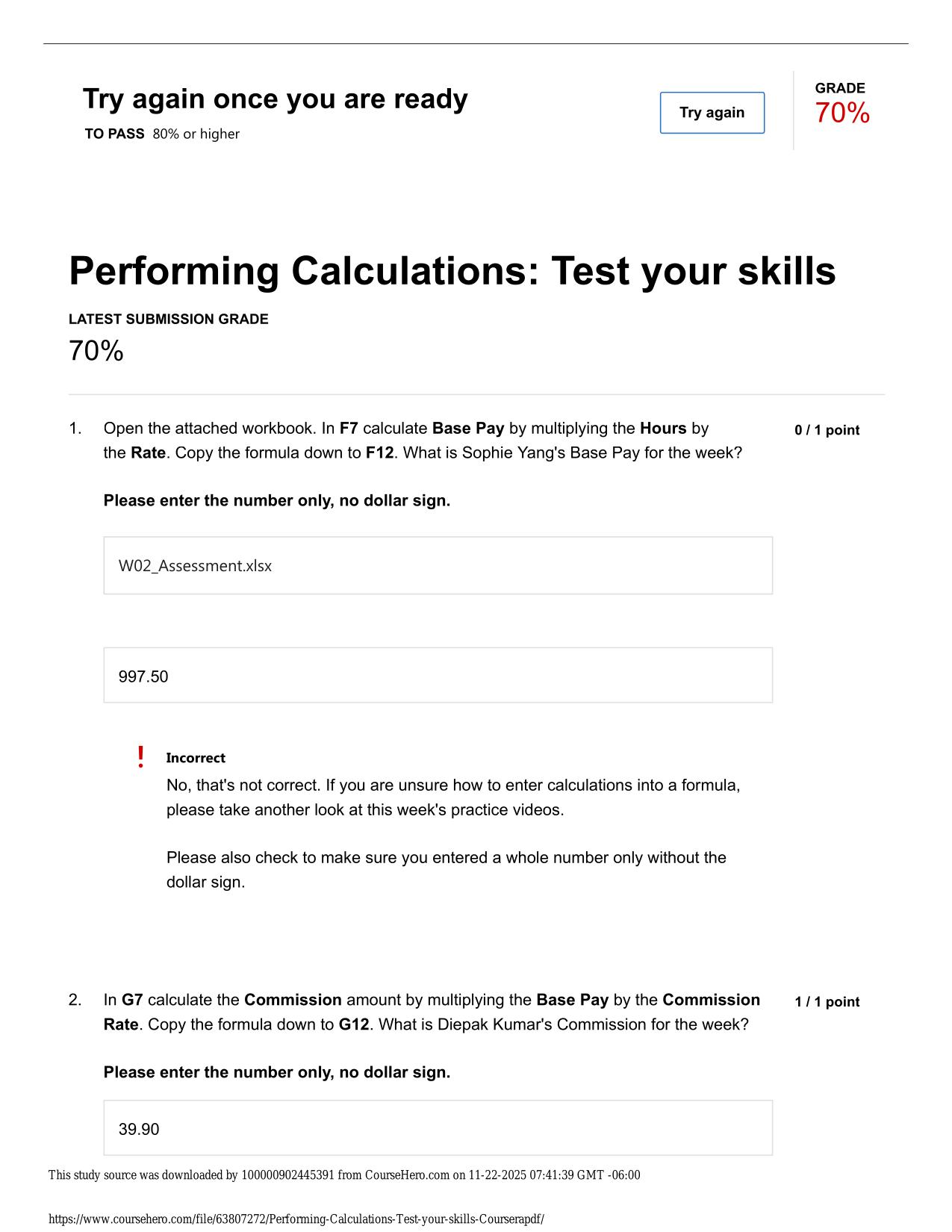
CYBER AWARENESS CHALLENGE ACTUAL 2025/2026 (KNOWLEDGE PRE-CHECK) QUESTIONS AND 100% CORRECT ANSWERS Which of the following is a best practice for managing connection requests on social networking sites? - Answer -Validate connection requests through ...
After purchase, you get:
✅ Instant PDF Download
✅ Verified answer explanations
✅ Refund if not Satisfied
✅ Prepared for 2025/2026 test cycle
Overview
The variety of items — from simple recall to advanced scenario evaluation — provides a realistic preparation experience. You're developing different thinking skills rather than just practicing one type of question repeatedly. This balanced approach ensures you're ready for the full spectrum of challenges the exam presents. Many test-takers find they're better prepared for unexpected question formats thanks to this diverse practice.
Who Is This For?
Created for exam takers seeking maximum exposure to typical Exam (elaborations) questions, rationales, and scenarios. People often use it to test their readiness before the actual exam. The complete coverage ensures thorough preparation. Built for independent learners, study groups, and classroom instructors who require reliable exam-prep content in CYBER AWARENESS CHALLENGE. Teachers often incorporate these materials into their lesson plans. The consistent quality makes it a trusted resource semester after semester.
Related Keywords
Detailed Study Description
Frequently Asked Questions
Document Information
| Uploaded on: | October 31, 2025 |
| Last updated: | November 17, 2025 |
| Number of pages: | 5 |
| Written in: | 2025/2026 |
| Type: | Exam (elaborations) |
| Contains: | Questions & Answers |
| Tags: | CYBER AWARENESS CHALLENGE ACTUAL 2025/2026 (KNOWLEDGE PRE-CHECK) QUESTIONS AND 100% CORRECT ANSWERS Which of the following is a best practice for managing connection requests on social networking sites? - Answer -Validate connection requests through another source if possible which of the following is an authoritative source for derivative classification? |
Seller Information

AdelineJean
User Reviews (0)
Exam (Elaborations)
$6.00
Bundle Deal! Get all 6 docs for just $18.00
Add to Cart
100% satisfaction guarantee
Refund Upon dissatisfaction
Immediately available after purchase
Available in Both online and PDF
$6.00
| 0 sold
Discover More resources
Available in a Bundle
Inside The Document
CYBER AWARENESS CHALLENGE ACTUAL 2025/2026 (KNOWLEDGE PRE-CHECK) QUESTIONS AND 100% CORRECT ANSWERS Which of the following is a best practice for managing connection requests on social networking sites? - Answer -Validate connection requests through another source if possible which of the following is an authoritative source for derivative classification? - Answer -Security Classification Guide Which of the following is a step you should NOT take to protect against spillage? - Answer -Purge any device's memory before connecting it to a classified network? Which best describes an insider threat? Someone who uses ____ access, ____, to harm national security through unauthorized disclosure, data modification, espionage, terrorism, or kinetic actions. - Answer -authorized, wittingly or unwittingly Which of the following is NOT a best practice for teleworking in an environment where Internet of Things (IoT) devices are present? - Answer -Use the devices' default security settings Which of the following is a best practice for using government e-mail? - Answer -Do not send mass e-mails How can you mitigate the potential risk associated with a compressed URL (e.g., TinyURL, goo.gl)? - Answer -Use the preview function to see where the link actually leads Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com
CourseHero & Studypool Unlocks
Get Unlocked CourseHero and Studypool documents files instantly to your email, simply by pasting your link and clicking "Unlock Now". Learn more on how to unlock here.