US NAVY CYBER AWARENESS CHALLENGE ACTUAL 2025/2026 Q&A
Course:
CYBER AWARENESS CHALLENGE
Institution:
CYBER AWARENESS CHALLENGE
US NAVY CYBER AWARENESS CHALLENGE ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS Which of the following is an example of behavior that you should report? -Planning an overseas vacation -Drinking alcohol socially -Expressing dislike of a recent P...
After purchase, you get:
✅ Instant PDF Download
✅ Verified answer explanations
✅ Refund if not Satisfied
✅ Prepared for 2025/2026 test cycle
Overview
Questions are arranged to build from basic concepts to more advanced challenges, making the learning curve smoother and more methodical. You'll notice your assurance growing naturally as you excel at each level before moving to the next. This scaffolding approach prevents that overwhelmed feeling that often comes with jumping into complex topics too quickly. Many learners appreciate how this progression mirrors the way we naturally learn - building step by step from simple to sophisticated.
Who Is This For?
US NAVY CYBER AWARENESS CHALLENGE ACTUAL / Q&A aspirants aiming to build both conceptual knowledge and exam strategy will find this document extremely useful. Many successful candidates have used similar materials in their preparation. The complete coverage ensures no important topics are missed. A recommended pick for anyone looking to review, reinforce, and learn thoroughly Exam (elaborations) exam topics using reliable practice content. Many educators suggest similar materials to their students. The trusted format has stood the test of time across multiple exam cycles.
Related Keywords
Detailed Study Description
Frequently Asked Questions
Document Information
| Uploaded on: | October 31, 2025 |
| Last updated: | November 17, 2025 |
| Number of pages: | 55 |
| Written in: | 2025/2026 |
| Type: | Exam (elaborations) |
| Contains: | Questions & Answers |
| Tags: | US NAVY CYBER AWARENESS CHALLENGE ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS Which of the following is an example of behavior that you should report? -Planning an overseas vacation -Drinking alcohol socially -Expressing dislike of a recent Presidential action -Bringing a phone into a prohibited area - Answer -Bringing a phone into a prohibited |
Seller Information

AdelineJean
User Reviews (0)
Exam (Elaborations)
$10.00
Bundle Deal! Get all 6 docs for just $18.00
Add to Cart
100% satisfaction guarantee
Refund Upon dissatisfaction
Immediately available after purchase
Available in Both online and PDF
$10.00
| 0 sold
Discover More resources
Available in a Bundle
Inside The Document
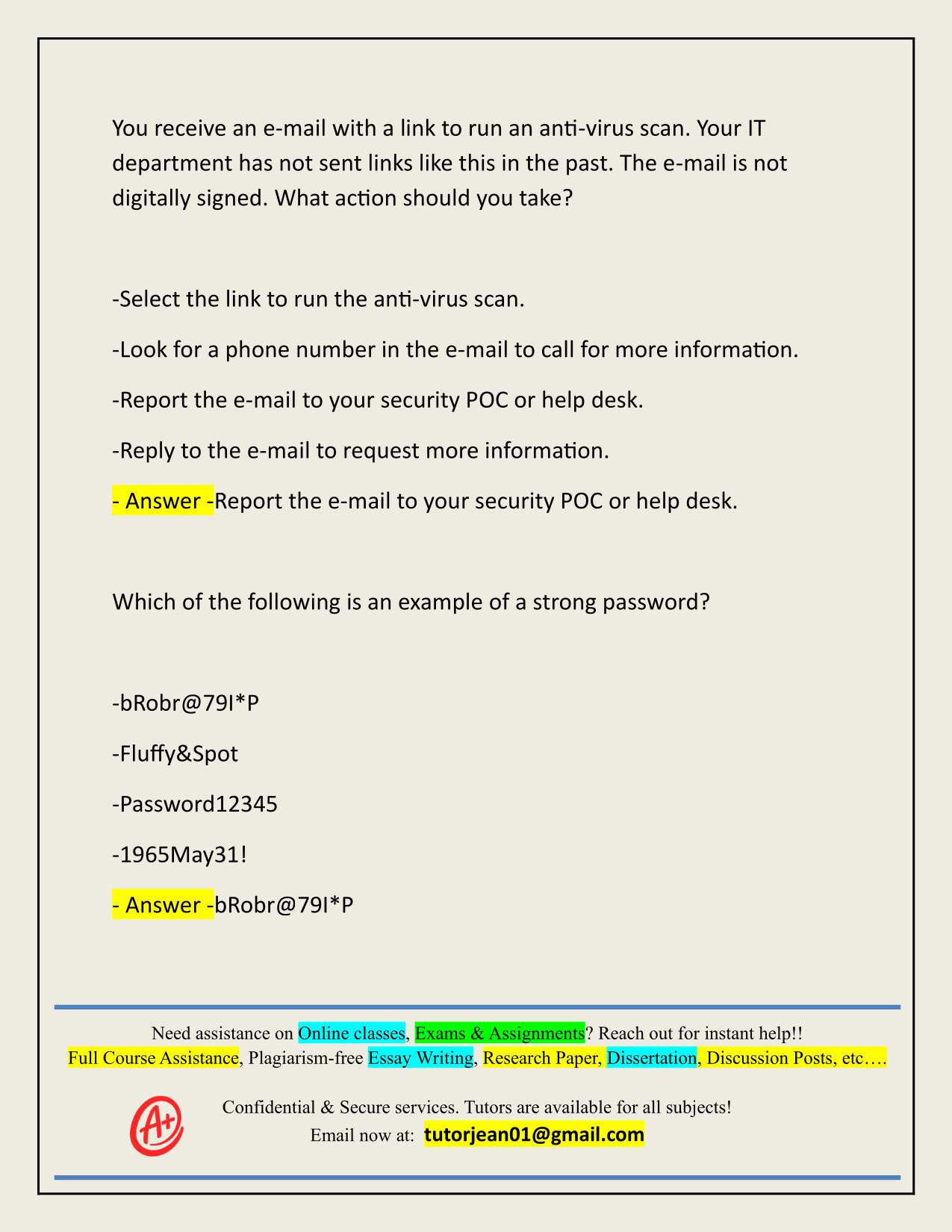
US NAVY CYBER AWARENESS CHALLENGE ACTUAL 2025/2026 QUESTIONS AND 100% CORRECT ANSWERS Which of the following is an example of behavior that you should report? -Planning an overseas vacation -Drinking alcohol socially -Expressing dislike of a recent Presidential action -Bringing a phone into a prohibited area - Answer -Bringing a phone into a prohibited area You receive an e-mail with a link to run an anti-virus scan. Your IT department has not sent links like this in the past. The e-mail is not digitally signed. What action should you take? -Select the link to run the anti-virus scan. -Look for a phone number in the e-mail to call for more information. -Report the e-mail to your security POC or help desk. -Reply to the e-mail to request more information. - Answer -Report the e-mail to your security POC or help desk. Which of the following is an example of a strong password? -bRobr@79I*P -Fluffy&Spot -Password12345 -1965May31! - Answer -bRobr@79I*P Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com Which of the following can be used to catalogue information about you? -Social networking sites -Audio-enabled digital assistants (e.g., Siri, Alexa) -Fitness trackers -All of these - Answer -All of these Which of the following is a best practice to protect your identity? -Throw credit card and bank statement in the trash -Carry your passport with you at all times -Enable data aggregation on sites when possible -Ask how information will be used before giving it out - Answer -Ask how information will be used before giving it out Which of the following describes Sensitive Compartmented Information (SCI)? -The requirement for access to SCI material are security clearance eligibility and need-to-know -SCI introduces an overlay of security to Top Secret, Secret, and Confidential information. -The determination that a piece of information is SCI is made at the organizational level. -SCI is a type of Controlled Unclassified Information (CUI). - Answer -SCI introduces an overlay of security to Top Secret, Secret, and Confidential information. Which of the following is the safest to share on a social media networking site? -Your birthdate -Your mother's maiden name -Your favorite movie -Your current location - Answer -Your favorite movie Need assistance on Online classes, Exams & Assignments? Reach out for instant help!! Full Course Assistance, Plagiarism-free Essay Writing, Research Paper, Dissertation, Discussion Posts, etc…. Confidential & Secure services. Tutors are available for all subjects! Email now at: tutorjean01@gmail.com
CourseHero & Studypool Unlocks
Get Unlocked CourseHero and Studypool documents files instantly to your email, simply by pasting your link and clicking "Unlock Now". Learn more on how to unlock here.